
Hewlett Packard Enterprise (HPE) is investigating a opportunity new breach following a menace actor set allegedly stolen knowledge up for sale on a hacking forum, boasting it includes HPE credentials and other sensitive facts.
The firm has instructed BleepingComputer that they have not observed any evidence of a safety breach and no ransom has been asked for, but it really is investigating the menace actor’s claims.
“We are mindful of the promises and are investigating their veracity,” HPE’s Sr. Director for World Communications Adam R. Bauer explained to BleepingComputer on Thursday.
“At this time we have not discovered evidence of an intrusion, nor any effect to HPE products or services. There has not been an extortion endeavor.”
When requested to offer more details relating to the company’s ongoing investigation, Bauer stated they experienced “very little new to share.”
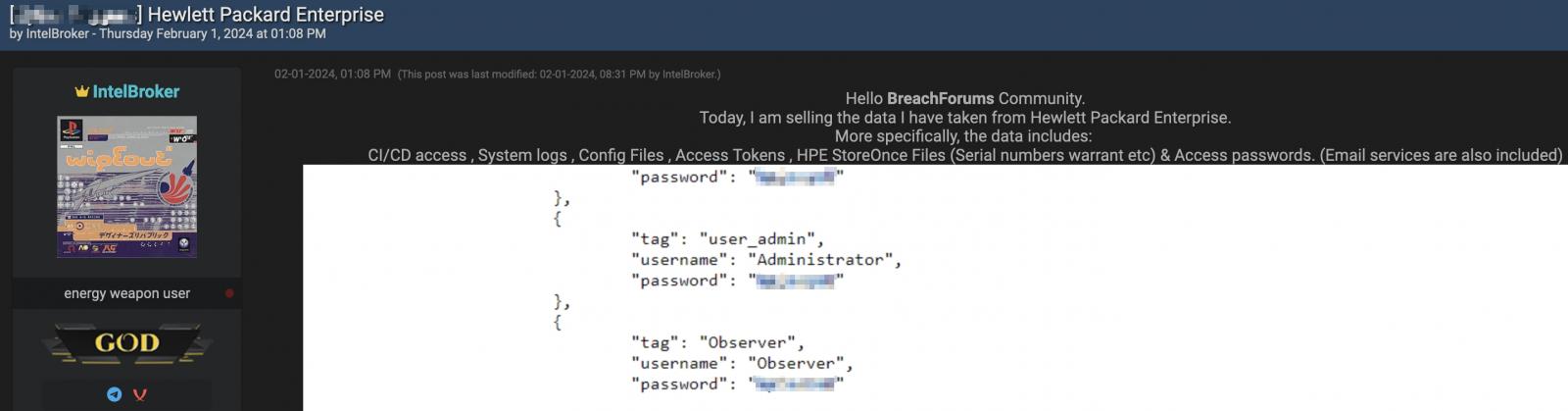
IntelBroker, the risk actor marketing the alleged HPE data, shared screenshots of some of the supposedly stolen HPE qualifications but has but to disclose the supply of the details or the technique made use of to obtain it.
“Right now, I am promoting the facts I have taken from Hewlett Packard Organization,” the threat actor claims in a submit on the hacking forum.
“Far more precisely, the info involves: CI/CD entry , Method logs , Config Information , Accessibility Tokens , HPE StoreOnce Files (Serial quantities warrant and so forth) & Obtain passwords. (E mail products and services are also included).”
IntelBroker is very best identified for the breach of DC Wellbeing Link, which led to a congressional hearing after it exposed the own knowledge of U.S. Residence of Representatives members and employees.
Other cybersecurity incidents connected to IntelBroker are the breach of the Weee! grocery service and an alleged breach of Typical Electrical Aviation.
Russian hackers breach HPE company e mail accounts
This investigation arrives immediately after HPE disclosed two weeks ago that the company’s Microsoft Business 365 email surroundings was breached in May perhaps 2023 by hackers the business considered to be element of the Russian APT29 hacking group joined to Russia’s Overseas Intelligence Services (SVR).
The corporation claimed the Russian hackers stole SharePoint documents and information from its cybersecurity crew and other departments and maintained obtain to its cloud infrastructure until finally December when HPE was once again alerted of a breach of its cloud-centered email surroundings.
“On December 12, 2023, HPE was notified that a suspected country-state actor had received unauthorized accessibility to the company’s Business 365 email environment. HPE promptly activated cyber reaction protocols to commence an investigation, remediate the incident, and eradicate the exercise,” HPE instructed BleepingComputer.
“By that investigation, which continues to be ongoing, we determined that this nation-state actor accessed and exfiltrated information starting in May 2023 from a smaller percentage of HPE mailboxes belonging to persons in our cybersecurity, go-to-industry, business segments, and other capabilities.”
Days ahead of HPE’s Russian hack disclosure, Microsoft disclosed a comparable breach where APT29 breached some of its corporate e mail accounts belonging to its leadership workforce and employees in the cybersecurity and authorized departments.
Microsoft later shared that the threat actors attained access to the corporate e-mail accounts just after hacking into a misconfigured test tenant account by brute forcing its password in a “password spraying” attack.
HPE was also breached in 2018 when APT10 Chinese hackers also hacked into IBM’s networks and made use of the obtain to hack into their customers’ devices.
Extra just lately, HPE disclosed in 2021 that information repositories of its Aruba Central network monitoring platform were being compromised, enabling attackers to entry details about monitored equipment and their areas.
Update February 05, 16:46 EST: After the report was released, Bauer also told BleepingComputer that the knowledge staying provided for sale on line was obtained from a “exam ecosystem.”
“Based mostly on our investigation so significantly, the info at problem seems to be connected to details that was contained in a examination environment. There is no indicator these claims relate to any compromise of HPE manufacturing environments or buyer information,” Bauer reported in a statement sent in excess of email.
“These are regional credentials utilised in an isolated exam setting and are not relevant to the generation ecosystem. In addition, these qualifications by itself would not allow for access to manufacturing environments as we have multi-layered protection steps in area. In addition, we never have any indicator that these statements relate to any compromise of customer facts. That explained, we have taken further actions to harden our environment further more in relation to the qualifications at problem.”